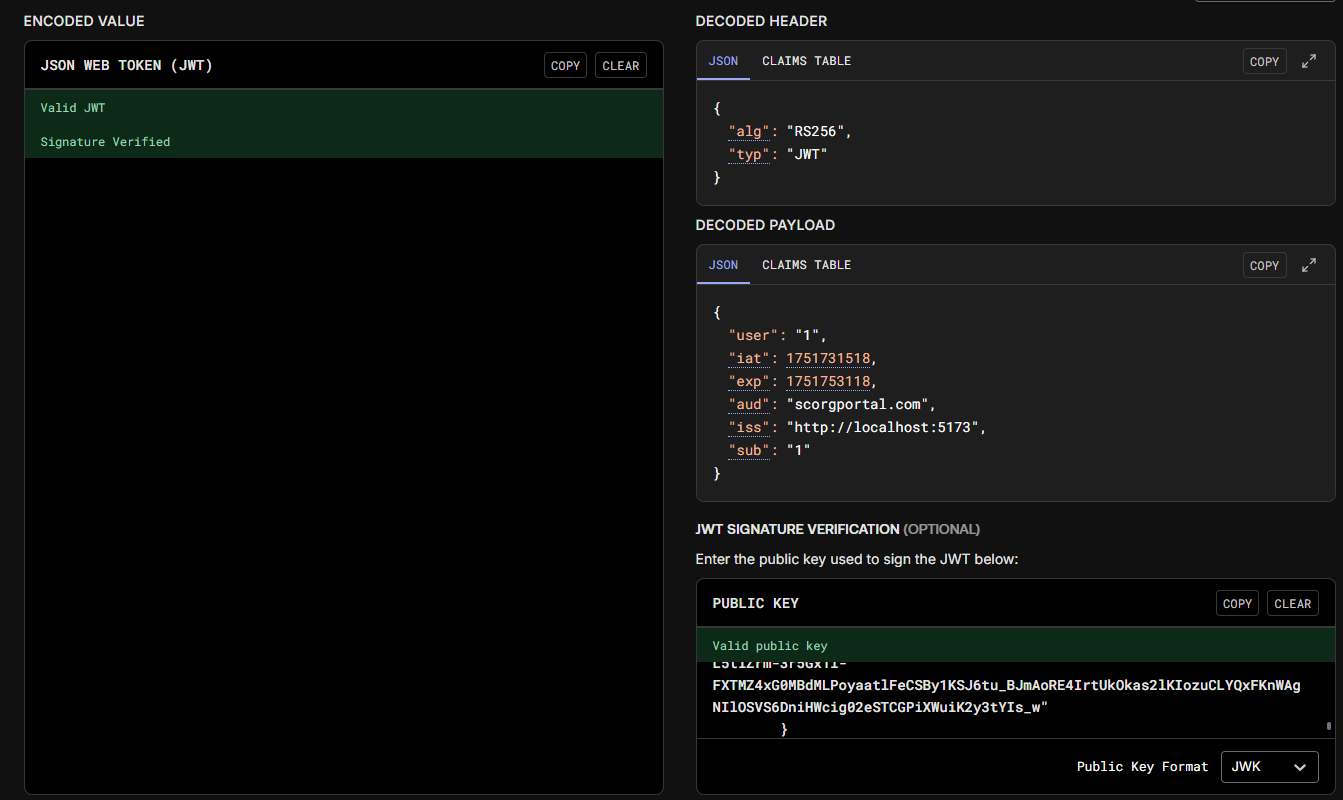
Help debugging custom JWT auth
auth.config.tssetAuthThe convex instance is a local development instance created with
npx convex dev --local --onceconvex/auth.config.tssetAuth call:
Any help is appreciated!!